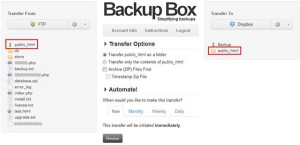
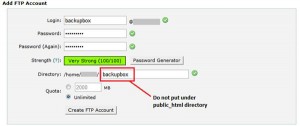
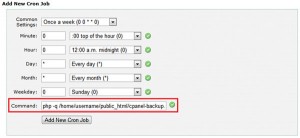
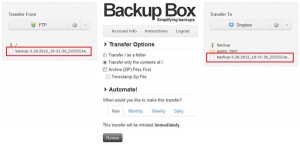
The DNS ( Domain Name System ) is a distributed system, used for translate domain names to IP and vice a versa
Network Scenario for this Setup
Master DNS Server IP: 10.10.10.20 ( ns1.example.net )
Slave DNS Server IP: 10.10.11.243 ( ns2.example.net )
Domain Name : demoexample.net ( For Testing Purpose )
Domain IP : 10.10.10.100 ( For Testing Purpose )
Install Required RPMS ( at Master and Slave Both )
Install bind packages at both Master and Slave dns servers using following commands.
# yum install bind bind-chroot
Setup Master (NS1) DNS Server
There are two types of configuration files in DNS.
- One is main dns configuration files named “named.conf”
- Another type of configuration file are called zone file. Which is individually created for all domains. named.conf keeps an entry for all zone files.
Configure named.conf using below configuration
# vim /var/named/chroot/etc/named.conf
Content of named.conf:
// /var/named/chroot/etc/named.conf
acl internals {
127.0.0.0/8;
10.10.10.0/24;
10.10.11.0/24;
115.254.78.93;
};
acl slaves {
10.10.11.243/32;
97.74.243.55/32;
10.10.10.0/24;
};
acl trusted {
10.10.11.240/28;
10.10.10.0/24;
};
options {
listen-on port 53 { 127.0.0.1; any; };
listen-on-v6 { any; };
# version "Please go Ahead";
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
# query-source port 53;
# query-source-v6 port 53;
allow-query { any; };
allow-recursion {
slaves;
trusted;
internals;
};
allow-transfer { slaves; };
};
#logging {
# channel default_debug {
# file "data/named.run";
# severity dynamic;
# };
#};
logging {
channel default_syslog { syslog local2; severity notice; };
category "default" { "debug"; };
category "general" { "debug"; };
category "database" { "debug"; };
category "security" { "debug"; };
category "config" { "debug"; };
category "resolver" { "debug"; };
category "xfer-in" { "debug"; };
category "xfer-out" { "debug"; };
category "notify" { "debug"; };
category "client" { "debug"; };
category "unmatched" { "debug"; };
category "network" { "debug"; };
category "update" { "debug"; };
category "queries" { "debug"; };
category "dispatch" { "debug"; };
category "dnssec" { "debug"; };
category lame-servers {null; };
category edns-disabled { null; };
channel "debug" {
file "/var/log/named/named.log" versions 2 size 1024m;
print-time yes;
print-category yes;
};
};
include "/etc/rndc.key";
controls {
inet 127.0.0.1 port 953 allow { localhost; };
};
view localhost_resolver {
match-clients { internals; };
match-destinations { localnets; };
# recursion yes;
include "/etc/named.rfc1912.zones";
include "/var/named/named.zones";
include "/var/named/named_new.zones";
};
view "external" {
match-clients { any; };
match-destinations { any; };
# recursion no;
include "/var/named/named.zones";
include "/var/named/named_new.zones";
};
# vim /var/named/named.zones
Content of named.zones:
zone "example.net" IN {
type master;
file "example.net.zone";
allow-transfer {
10.10.11.243;
};
};
zone "nethost.com" IN {
type master;
file "nethost.com.zone";
allow-transfer {
10.10.11.243;
};
};
zone "testreflexologydayspa.com" IN {
type master;
file "testreflexologydayspa.com.zone";
allow-transfer {
10.10.11.243;
};
};
zone "nethost.net" IN {
type master;
file "nethost.net.zone";
allow-transfer {
10.10.11.243;
};
};
# vim /var/named/named_new.zones
Content of named_new.zones:
zone "sahana.on.com"{
type master;
file "s/p-sahana.on.com";
also-notify { 64.68.200.91; };
allow-transfer {
10.10.11.243;
64.68.200.91;
72.52.2.1;
64.68.196.10;
64.68.192.210;
};
};
zone "oahanacolleges.com"{
type master;
file "o/p-oahanacolleges.com";
also-notify { 64.68.200.91; };
allow-transfer {
64.68.200.91;
10.10.11.243;
72.52.2.1;
64.68.196.10;
64.68.192.210;
};
};
zone "1101baybay.ca"{
type master;
file "1/p-1101baybay.ca";
allow-transfer {
10.10.11.243;
};
};
Create a zone file for your domain “example.net”
# vim /var/named/example.net
Content of zone file:
$ORIGIN .
$TTL 600 ; 10 minutes
example.net IN SOA sys.example.net. root.sys.example.net. (
2014021800 ; serial
7200 ; refresh (2 hours)
3600 ; retry (1 hour)
43200 ; expire (1 week)
3600 ; minimum (1 hour)
)
NS ns1.example.net.
NS ns2.example.net.
A 10.10.10.32
MX 0 example-net.mail.eo.outlook.com.
TXT "v=spf1 include:outlook.com ~all"
SRV 100 1 5061 sipfed.online.lync.com.
$ORIGIN example.net.
adminfs A 10.10.11.29
autodiscover CNAME autodiscover.outlook.com.
home A 10.10.10.95
ns1 A 10.10.10.20
ns2 A 10.10.11.243
ns3 A 10.10.11.243
webmail IN A 10.10.10.64
* IN A 10.10.10.64
Create a zone file for your reverse domain “10.10.10.in-addr.arpa.zone”
# vim /var/named/10.10.10.in-addr.arpa.zone
Content of zone file:
$ORIGIN .
$TTL 600 ; 10 minutes
10.10.10.in-addr.arpa IN SOA ns1.example.net. root.example.net. (
2014032001 ; serial
7200 ; refresh (2 hours)
3600 ; retry (1 hour)
43200 ; expire (1 week)
3600 ; minimum (1 hour)
)
NS ns1.example.net.
NS ns2.example.net.
$ORIGIN 10.10.10.in-addr.arpa.
100 PTR cpanel.midinet.com.
120 PTR winpl.midinet.com.
150 PTR urban.ca.
20 PTR ns1.example.net.
85 PTR ratherlaugh.com.
86 PTR statusopenged.com.
87 PTR open.statusopenged.com.
88 PTR offresgetsmain.net.
89 PTR stat.offresgetsmain.net.
227 PTR devanorth.com.
84 PTR wiki.eausergroup.org.
55 PTR equipmentscheduling.com.
Start named service
Startnamed(bind) service using following command and setup auto start on system boot.
# /etc/init.d/named restart
# chkconfig named on
Setup Slave (NS2) DNS Server
At slave dns server you need to updatenamed.conf file only. All zone files will automatically synced from master dns server. Any changes done on Master will reflect on slave after a specified time interval.
Configure named.conf using below configuration
# vim /var/named/chroot/etc/named.conf
Content of named.conf
// /var/named/chroot/etc/named.conf
acl trusted {
10.10.11.240/28;
10.10.10.0/24;
10.10.11.0/24;
};
options {
listen-on port 53 { 127.0.0.1; any; };
version "Please go Ahead";
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
# query-source port 53;
# query-source-v6 port 53;
allow-query { any; };
allow-transfer { none; };
allow-recursion { trusted;};
allow-notify {trusted;};
};
#logging {
# channel default_debug {
# file "data/named.run";
# severity dynamic;
# };
#};
logging {
channel default_syslog { syslog local2; severity notice; };
category "default" { "debug"; };
category "general" { "debug"; };
category "database" { "debug"; };
category "security" { "debug"; };
category "config" { "debug"; };
category "resolver" { "debug"; };
category "xfer-in" { "debug"; };
category "xfer-out" { "debug"; };
category "notify" { "debug"; };
category "client" { "debug"; };
category "unmatched" { "debug"; };
category "network" { "debug"; };
category "update" { "debug"; };
category "queries" { "debug"; };
category "dispatch" { "debug"; };
category "dnssec" { "debug"; };
category lame-servers {null; };
# category edns-disabled { null; };
channel "debug" {
file "/var/log/named/named.log" versions 2 size 150m;
print-time yes;
print-category yes;
};
};
include "/etc/rndc.key";
controls {
inet 127.0.0.1 port 953 allow { localhost; };
};
view localhost_resolver {
match-clients { localnets; };
match-destinations { localhost; };
# recursion yes;
include "/etc/named.rfc1912.zones";
include "/var/named/named.zones";
include "/var/named/named_new.zones";
};
view "external" {
match-clients { any; };
match-destinations { any; };
include "/var/named/named.zones";
include "/var/named/named_new.zones";
};
# vim /var/named/named.zones
zone "example.net" IN {
type slave;
masters { 10.10.10.20; };
file "example.net.zone";
};
zone "nethost.com" IN {
type slave;
masters { 10.10.10.20; };
file "nethost.com.zone";
};
zone "reflexologydayspa.com" IN {
type slave;
masters { 10.10.10.20; };
file "reflexologydayspa.com.zone";
};
zone "nethost.net" IN {
type slave;
masters { 10.10.10.20; };
file "nethost.net.zone";
};
zone "westmountroutes.com" IN {
type slave;
masters { 10.10.10.20; };
file "westmountroutes.com.zone";
};
zone "siteinmotionhosting.com" IN {
type slave;
masters { 10.10.10.20; };
file "siteinmotionhosting.com.zone";
};
# vim /var/named/named_new.zones
zone "iaaos.ca"{
type slave;
masters { 10.10.10.20; } ;
file "i/s-iaaos.ca";
};
zone "saco.ca"{
type slave;
masters { 10.10.10.20; } ;
file "o/s-saco.ca";
};
zone "schooldelontario.ca"{
type slave;
masters { 10.10.10.20; } ;
file "c/s-schooldelontario.ca";
};
zone "saco.on.ca"{
type slave;
masters { 10.10.10.20; } ;
file "s/s-saco.on.ca";
};
zone "ontarioschool.ca"{
type slave;
masters { 10.10.10.20; } ;
file "o/s-ontarioschool.ca";
};
zone "1101bay.ca"{
type slave;
masters { 10.10.10.20; } ;
file "1/s-1101bay.ca";
};
zone "1101bay.com"{
type slave;
masters { 10.10.10.20; } ;
file "1/s-1101bay.com";
};
# vim /var/named/example.net.zone
$ORIGIN .
$TTL 600 ; 10 minutes
example.net IN SOA ns1.example.net. root.ns1.example.net. (
2014021800 ; serial
7200 ; refresh (2 hours)
3600 ; retry (1 hour)
43200 ; expire (1 week)
3600 ; minimum (1 hour)
)
NS ns1.example.net.
NS ns2.example.net.
A 10.10.10.32
MX 0 example-net.mail.eo.outlook.com.
TXT "v=spf1 include:outlook.com ~all"
SRV 100 1 5061 sipfed.online.lync.com.
$ORIGIN example.net.
adminfs A 10.10.11.29
autodiscover CNAME autodiscover.outlook.com.
home A 10.10.10.95
ns1 A 10.10.10.20
ns2 A 10.10.11.243
ns3 A 10.10.11.243
webmail A 10.10.10.64
* A 10.10.10.64
# vim /var/named/10.10.10.in-addr.arpa.zone
$ORIGIN .
$TTL 600 ; 10 minutes
10.10.10.in-addr.arpa IN SOA ns1.example.net. root.example.net. (
2014032001 ; serial
7200 ; refresh (2 hours)
3600 ; retry (1 hour)
43200 ; expire (1 week)
3600 ; minimum (1 hour)
)
NS ns1.example.net.
NS ns2.example.net.
$ORIGIN 10.10.10.in-addr.arpa.
100 PTR cpanel.midinet.com.
120 PTR winpl.midinet.com.
150 PTR urban.ca.
20 PTR ns1.example.net.
85 PTR ratherlaugh.com.
86 PTR statusopenged.com.
87 PTR open.statusopenged.com.
88 PTR offresgetsmain.net.
89 PTR stat.offresgetsmain.net.
227 PTR devanorth.com.
84 PTR wiki.eausergroup.org.
55 PTR equipmentscheduling.com.
Start named Service
Startnamed(bind) service using below command.
# /etc/init.d/named restart
# chkconfig named on
After restartingnamedservice, Check zone files on slave dns server at /var/named/chroot/var/named/slaves/.
Step 4: Finally Test Your DNS Setup
Query to your Master and Slave DNS Server directly using following commands, You will get the same resonse from both servers.
Syntax: nslookup <domainname.com> <dns server name/ip>
Query to Master DNS Server:
# nslookup demoexample.net 10.10.10.20
Server: 10.10.10.20
Address: 10.10.10.20#53
Name: demoexample.net
Address: 10.10.10.100
Query to Slave DNS Server:
# nslookup demoexample.net 10.10.11.243
Server: 10.10.11.243
Address: 10.10.11.243#53
Name: demoexample.net
Address: 10.10.10.100
Above outputs is showing that dns server has successfully resolved domain demoexample.net from master and slave dns servers.